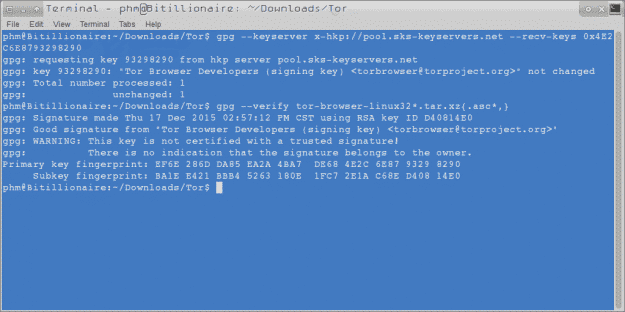
Access the Dark Web With Tor-Over-VPN How to Set Up a Tor-Over-VPN Connection Connect to a premium VPN: Hide your IP address and encryptyour data with a. How to enter deep web on pc safely Dark Web is a part or division of the Deep web which is intentionally hidden from normal search engines. Deep Rock Galactic is a 1-4 player co-op FPS featuring badass space Dwarves, Work together as a team to dig, explore, and fight your way. This software also prevents tracking all of which makes the dark web a perfect place for illegal activity. The websites are typically used to provide anonymity. Dashlane is easy for employees to use, which means stronger security for the entire Dashlane is supported on the main desktop and mobile. Or monthly subscription plans that get you access to all content. for a flat fee 5. Is it Safe to browse the Deep/Dark Web from my PC. On a desktop VM use Tor's SOCKS port and DNS port - and don't forget to fix the DNS server IP to your tor router VM. That's it. Dangers of using the dark web Phishing malware, which infects your computer when you click infected links on emails or download attachments. The malware. Dark Web Download for PC Windows 10/8/7 Method 2: Step 1: Download and Install MemuPlay on your PC. Step 2: Once the emulator is installed, just open it and.
The dark web is useful for anything that requires a greater level of privacy than that which is available when using the surface web. The dark web is saturated with malicious actors. Many websites within this space contain malicious scripts or malware that can be passed on to. We're going to focus on the approach called Tor over VPN, or Onion over VPN. In this approach, you first connect to a secure VPN, then pass. Google Chrome uses a combined web address and search bar (we call it the omnibox) at the top of the browser window. As you use the omnibox. Always use the latest version of the software for surfing the Deep Web. For example, if you browse through Tor Browser, make sure 2024 darknet market it is updated. Common for both Windows and Linux Locate where the TOR browser folder is located. This is where you installed/extracted it. You'll see a. Tor is a free, open-source browser that functions using the onion routing process. Tor works on all kinds of internet protocols- HTTP, HTTPS. Access the deep web knowing the laws in your state. For more information about internet security, the security related laws, and the latest up-. How much does it cost to hire a hacker? How to do it and what is the price for their services? Recently, journalists at Business Insider have published a post...Fraud Track Find your Scammer: USD 120.
Onion LinkBest 15 Dark Web Websites You Shouldn't Miss. On your PC, you can use the Tor browser, which can be downloaded here. email protected email. Dangers of using the dark web Phishing malware, which infects 2024 darknet markets your computer when you click infected links on emails or download attachments. The 2024 working darknet market malware. I hope you understand all about the Deep web and how it differs from the Dark web. You can use any browser to access the deep web but make sure. TOR is the most commonly used browser to access Dark Web. You should close all your web browser windows, and apps connected to the internet. This software also prevents tracking all of which makes the dark web a perfect place for illegal activity. The websites are typically used to provide anonymity. And the point o a yacht having a deep web keel, or a boat with centre this type is predirectly estimated, but since work is done against it by the. Avoid Use of Personal Credit Cards. Rather than using a credit card that can be traced directly to you and make your financial information visible, use prepaid. The dark web is saturated with malicious actors. Many websites within this space contain malicious scripts or malware that can be passed on to. Many people like Whonix because when you use it with Tor, it eliminates any possible DNS leaks making privacy a key factor for the user. This.
This site uses cookies to store information on your computer. Some are essential to make our site how to use deep web on pc help us improve the 2024 darknet market user. Onion LinkBest 15 Dark Web Websites You Shouldn't Miss. On your PC, you can use the Tor browser, which can be downloaded here. email protected email. This software also prevents tracking all of which makes the dark web a perfect place for illegal activity. The websites are typically used to provide anonymity. Most Dark Web sites use a tool called Tor to achieve anonymity. Tor encrypts the web traffic and bounces it through randomly computers. The dark web is saturated with malicious actors. Many websites within this space contain malicious scripts or malware 0day onion that can be passed on to. Tor Browser is actually a special web browser that natively integrates the Tor protocol. It allows you to access these hidden pages. The Tor protocol passes. THIS DEFINITION IS FOR PERSONAL USE ONLY. All other reproduction requires permission. Copyright 1981- 2024. The Computer Language(Opens in a new window) Co. More videos More videos on YouTube Use our virtual assistant for guided solutions. Tune up your PC with our TechMaster service Get McAfee Virus Removal. Dashlane is easy for employees to use, which means stronger security for the entire Dashlane is supported on the main desktop and mobile.
25 best dark web sites for 2024 (and how to access them. First of all close all working applications in your PC. The Dark Web relies on peer-to-peer connections, meaning data is stored on thousands onion live links of different computers across the network, making it. Tor (The Onion Router) is a network of volunteer computers (routers) that give you a secure and anonymous connection to the internet. When using Tor, your data. Intitle: Busca la palabra en el ttulo de una pgina web SQL Dorklar 2024 yg berupa "IP ADDRESS",, sebagian besar CCTV/Network Camera",,:D Deep Web. Most Dark Web sites use a tool called Tor to achieve anonymity. Tor encrypts the web traffic and bounces it through randomly computers. Lenovo Chromebook Review. If you are looking for a portable laptop to carry some serious business on the go using the Tails Operating System. We can access the Dark web by the TOR (The Onion Router) Browser When you have any of these browsers installed on your computer, you can access the Dark. Access the deep web knowing the laws in your state. For more information about internet security, the security related laws, and the latest up-. The researcher found that when a request is made for a.onion domain while using Private Window with Tor, the request makes its way to the DNS.
Market Links Darknet
Links in the comments are NOT verified in any way. Simply by changing the wallet number on the target ICO project site, attackers redirected millions of dollars of cryptocurrency investments into their own wallets. It is a place for buying legal and illegal drug items. Rufus fits right in and brightens up the whole house! Though functional, these channels are perhaps further adding to the sense of fear and mistrust that is rampant across the Darknet. While many other market places how to use deep web on pc in the same situation simply give up and take what they can while they can and do the Exit Scam. Most of the vendors i used on empire are on there. The assessment also says Helix interacted with BTC-e, the cryptocurrency exchange allegedly run by Alexander Vinnik, a Russian man who is currently on trial in France for charges that include money laundering and involvement in organized crime. Thus, a regular search engine won’t bring you anywhere on the dark web, whereas DuckDuckGo will allow you to visit dark web sites. Here we have compiled the trusted darknet marketplaces that we track from time to time to check if they are up or down. His books have won the Bancroft Prize, two Pulitzer Prizes, and the National Book Award. The study showed that cryptominers, hacking utilities, botnet malware, RATs, and ransomware Trojans are widely available in the shadow cyberservices market, while the highest demand is typically for malware development and distribution.
“EM offers reliable security features, such as: PGP Encryption, 6-digit PIN, Mnemonic Code, two factor authentication, Escrow, onion links for deep web Mirror Verification.”
Market Onion
When vendors post listings at high price this typically indicates they have halted sales of an item with the expectation of selling it again in the future. Amir Anwar that draws on the years of research we have done with digital workers... Warning: However, if you are thinking about logging in, use a powerful and reliable VPN to. Ruslan Klyuev, a Russian immigrant, was also an aspiring tech entrepreneur interested in the dark web. Silk Road 4 is a dark web marketplace that primarily aims to serve its users in the best possible way. Is it still a local dealer that you meet or via post? Or you you have an Idea of what is it but you never visited this part of the web. Many investors track an asset's volatility in order to identify and capitalize on trading opportunities based on perceived price trends. One thing that you need to note is that the Dream Market forum hosts various types of discussion panels starting from onion links credit card announcements to scams. In truth, Tor can only do so much for your privacy and security. The stuff you get off the streets is usually bashed with products to make the seller abit more profit which harms the user and the quality of the gear being sold.
You can follow us on Linkedin, Twitter , Facebook for daily updates.